Configuring SSO with Azure EntraID with SAML
This article guides Admin users step-by-step on how to configure SSO using Azure EntraID with SAML
Why set up single sign-on?
Single sign-on (SSO) allows EdApp to identify users through an external Identity Provider (IDP).
Instead of manually registering learners, users are directed to their company identity portal, fill in their company login details, and are redirected back to EdApp. This enables a user to log in to multiple systems via a single portal. On EdApp's side, a user is internally created to match the user's details sent back from the IDP.
If you’d like domain recognition enabled for SSO, please reach out to us via live chat or your EdApp program manager - we would be happy to help.
Ensure the person setting up SSO has admin privileges to both EdApp and the SSO provider.
Contents
Configure SSO in Azure AD
First, let’s start with setting up SSO in Azure AD (we’ll move on to setting this up in EdApp once this part is completed).
Step 1: Sign in to the Azure portal using your Azure Active Directory administrator account. Browse to the Active Directory > Enterprise Applications > New application > Non-gallery application section.
Step 2: Fill in "EdApp" as the application name, select Add.
Azure portal will redirect to the app overview page. Select Single sign-On > SAML
Step 3: Update Basic SAML Configuration
-
Fill in Identifier (Entity ID) with https://web.edapp.com/{companyID}.
You can replace company ID above with your organization's company ID e.g. https://web.edapp.com/acmeventures
-
Fill in Reply URL with https://api.edapp.com/sso-saml-callback/<unique-company-identifier>
-
Fill in Logout URL with https://api.edapp.com/sso-logout/<unique-company-identifer>
-
The following example has <unique-company-identifier> as uniqueEdCustomerCompanyId you can make this up but ensure that it is identifiable and easy for your learners to type in e.g. companyname
Step 4: Download Certificate (Base64) from SAML Signing Certificate section.
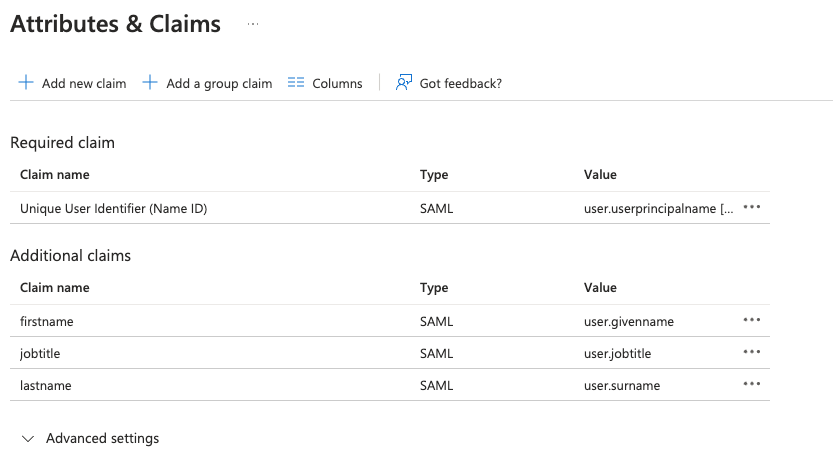
You can send additional information about your learners via custom fields including job title, first name, last name, active status or any custom fields you'd like. You can send these values as custom claims. The name of the claim needs to be exactly the same as the field name in EdApp. Also, the namespace of the claim needs to be blank.
This custom field data can then be used to automate user management through dynamic user groups. You can create criteria based rules on dynamic user groups to automatically assign learners to courses based on their information. Read more on dynamic user groups here.
Example
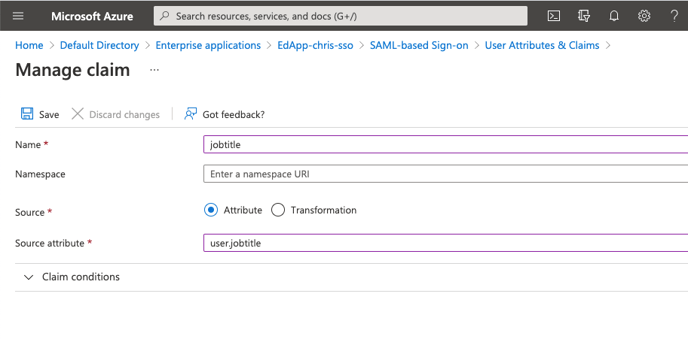
The firstname and lastname fields are supported out of the box in EdApp and can be passed as shown in the example below. In this example, the additional field "jobtitle" is passed as a claim as well and if configured in EdApp as a custom field it will be populated as soon as the user logs in using SSO.
Consider yourself halfway done! Now that we’ve managed to set up SSO in Azure AD, we’re ready to configure SSO in EdApp.
Configure SSO in EdApp
Step 1: Sign in to Ed LMS using your Ed Admin account, and click on the dropdown arrow located on the upper right of your screen. Select Single Sign-On.
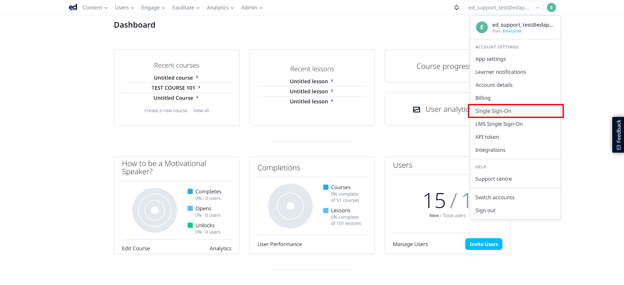
Step 2: Click on the Connect with SAML

Step 3: You’ll then arrive to your Single Sign-On page, where you can tick the box next to Enable Single Sign-On in order to expand the page to see the SSO fields below:
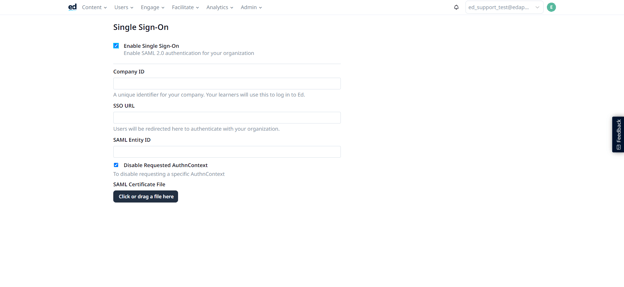
Step 4: Fill in Company ID
The company ID (on the admin portal) or business ID (on the learner's app) can be anything you want. Company ID and business ID are interchangeable terms on EdApp.
You must ensure this matches what you've used in your specific IDP, i.e. if you use "acmeventures" in the company ID in EdApp, make sure it's also "acmeventures" in your SSO provider.
It can be used by your learners at the login page, so it is important to choose a company ID that is easy to remember for your learners.
The company ID is also used to identify your account in EdApp when your IDP calls our API to authenticate the user. The ACS (Reply) URL field in your IDP specifies the endpoint in EdApp. The format in your IDP is https://api.edapp.com/sso-saml-callback/{COMPANY-ID}
If your company ID in EdApp is "acmeventures", your ACS (Reply) URL in your IDP would be https://api.edapp.com/sso-saml-callback/acmeventures
Step 5: Fill in SSO URL with the Login URL from Set up EdApp section.
Step 6: Fill SAML Entity ID with https://web.edapp.com/{companyID}.
You can replace company ID above with your organization's company ID e.g. https://web.edapp.com/acmeventures
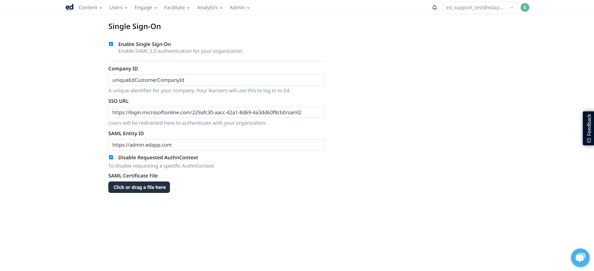
Step 7: upload your SAML certificate by clicking the upload button at the bottom of the page.
.png?width=688&height=198&name=image%20(54).png)
Reminder: Learner SSO works ONLY with .cer, .crt and .pem file certificates. If the certificate you downloaded in Step 7 is not a .cer, .crt and .pem file you may need to change its file extension.
Congratulations! You’ve just configured your EdApp account with SSO, using Azure AD. At this point, we recommend completing a round of successful testing by attempting login via SSO.
If you get stuck at any point along the way, be sure to reach out to our live chat desk, or your EdApp account manager - we’d be happy to lend a helping hand. Additionally, feel free to share this Learner Guide for logging into EdApp using SSO with your users.